
Sacrifice some piece of your privacy for some ‘quick instant loan to MPESA’. The year is 2019, the bloom of mobile instant loan apps which require your ID number, email, phone number and some interesting permission to your android device.
Requested Permissions
- SYSTEM_ALERT_WINDOW
- GET_TASKS
- CAMERA
- GET_ACCOUNTS
- READ_PHONE_NUMBERS
- ACCESS_NETWORK_STATE
- READ_PHONE_STATE
- INTERNET
- WRITE_EXTERNAL_STORAGE
- READ_EXTERNAL_STORAGE
- READ_CONTACTS
- ACCESS_COARSE_LOCATION
- ACCESS_FINE_LOCATION
- BIND_GET_INSTALL_REFERRER_SERVICE
You can look up what the permissions mean here : android developer docs After the app checks on your eligibility to be offered the requested loan amount. If successfull the funds are instantly transferred to your MPESA. Accepting the absurd interest rate and penalty if you default. With popular apps like Tala and Branch many similar applications have been lauched into the playstore some looking like outright scams. And the applications seem to be built using Rapid Android Application Development Frameworks. Which allow you to create an android app with little or sometimes writing no code.
Let’s look at Ganji, with thousands of downloads was popular on playstore. Never seen it before, so I decided to take a look at it.
Mostly I read on the apps reviews to find out what the user experience is . Seemed sane with the common “ why have you not given me a loan yet I qualify “ rants
🪲 Foreplay : static analysis
HASH
MD5: 2f11e6e52ba1ab6db967b841e395d22fSHA1: 37806fe466c8252934ead66071aab4fd584d0647SHA256: 3750e569684cb2fec0291f19725476b9b37d777c73920b0aff6c8b0448fc0253
APP INFORMATION
Package Name: com.ganjipayments
Android Version Name: 1.1.1.16
Now comes the interesting bit, after looking into some of the url the android application was interacting with , I immediatly had a smirk😏 on my face.Well boys and girls this seems like it isn’t going to take much long.
Diving into res/values/strings.xml, where all application strings are; I saw this gem 🙅🏽♀️ https://ganji-35361.firebaseio.com/ 🙅🏽♀️
Appending .json to the url after the trailing slash, making it https://ganji-35361.firebaseio.com/.json dumped all data in the database on the web. Simply put ,the database is publicly exposed and an attacker can very easily perform queries into the database , create, update and delete data from the database.
I wasn’t going to do that because of the ‘ethics’, what did I find though :
This is where i’ll throw in the phrase , “even a kid could do it” , no need for hooking up debuggers or even deobfuscating the source code
📑 findings
The database contained information about the Employees, Clients and Customer support messages.
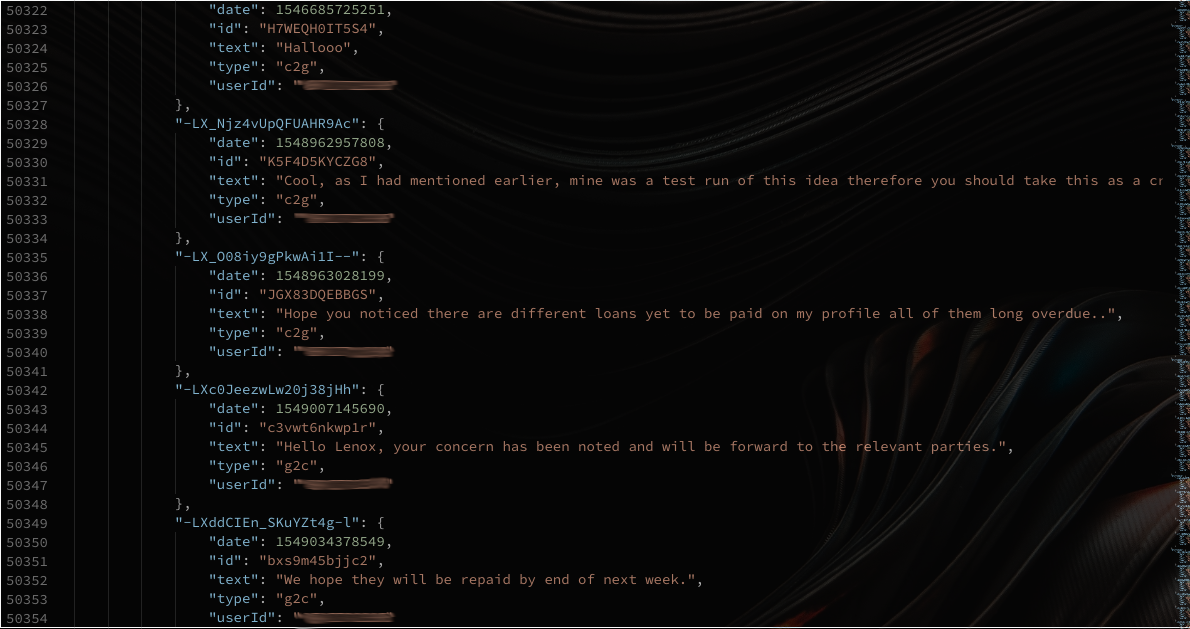
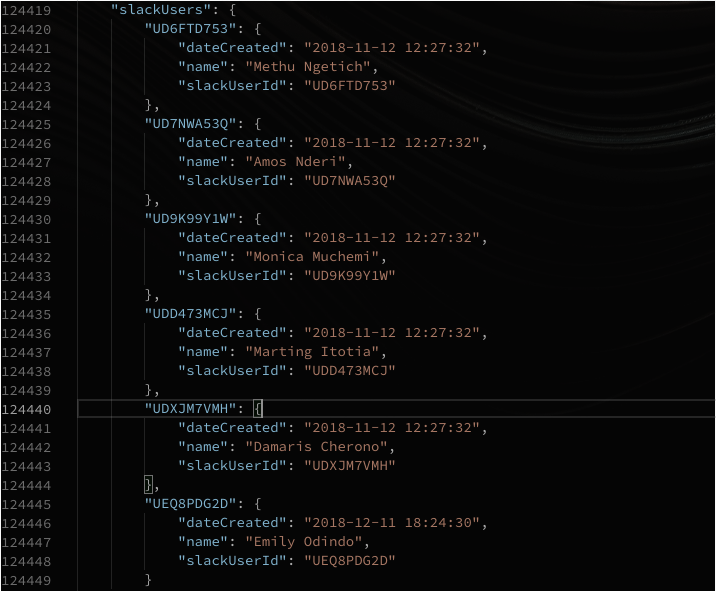
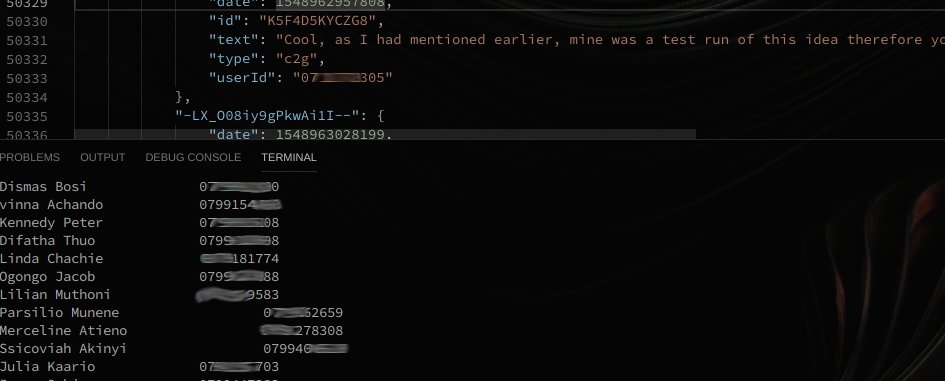
Well, imagine all these people having their debt’s cleared, I guess I wasn’t Joker at the moment more of a good will cast. I repored the issue and this is how it went.
Parting ways
bug report and disclosure
I emailed the customer support team and fortunately they got back to me . Wanted this to be wrapped up as quick as possible.
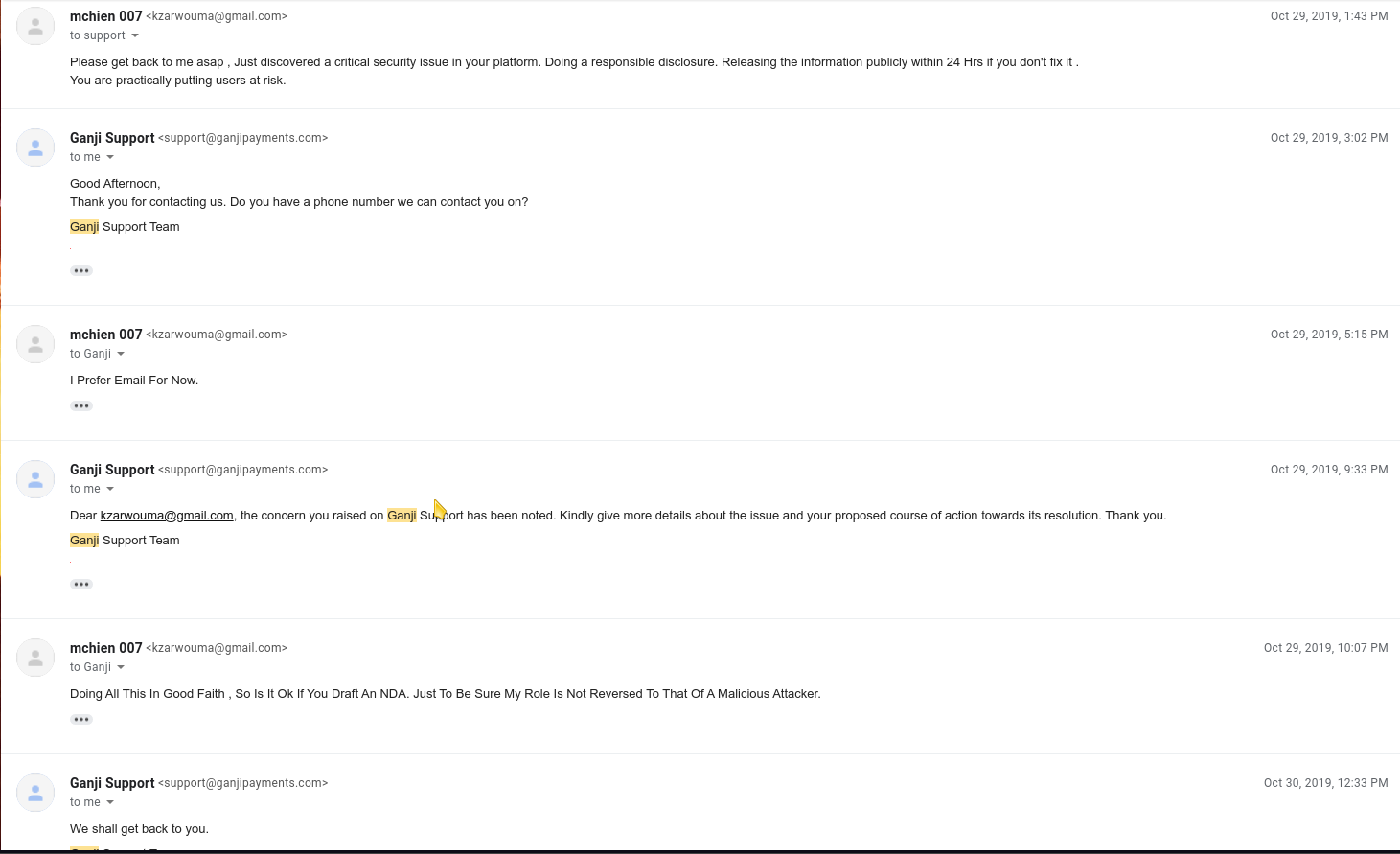
Couldn’t wait for them to take their time to fix it . Posted it on my Twitter and it got fixed.
Fixing it .
You can read firebase security rules.
Till next time, ✌🏽 adios